
SpacialSec CTI blog
The Black Team Ops Honeypot

The Black Team Ops Honeypot

Introduction
On October 8th, 15:44PM UTC, a member of SpacialSec was shitposting, specifically by tweeting a review of the CBTO (Certified Black Team Operator) certification and associated course, Black Team Ops 1 (A parody of ZeroPointSecurity's Red Team Ops).
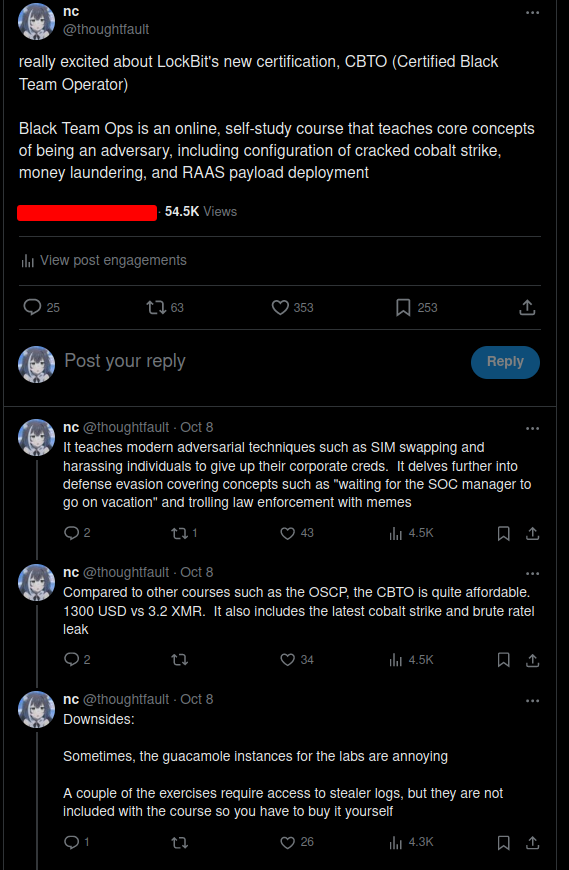
We (incorrectly) assumed this would be obvious satire to our viewers, but we were surprised when we received a plethora of messages asking for access to the course. This was distinct from those who understood the post to be satire and were playing along.
It seemed that this tweet was going far beyond the intended audience of those who were at least familiar the ZeroPointSecurity's CRTO course to the dreaded "skids" who showed actual interest in the course.
Interested how far we could take this, we decided it would be funny to edit the HTML of the pages from the legitimate "Red Team Ops" course by ZeroPointSecurity. We replaced content related to red teaming with techniques that would most likely be criminal in nature, including a section on SIM swapping, money laundering and ransomware deployment.
At October 8th, 11:21 PM UTC (About 5 hours after the initial post), we posted a fake course "sneakpeak".

This raked even more messages asking for the course, as well as increasing engagement for the original post! The SpacialSec CTI team identified this as a golden opportunity to create a honeypot.
How to bootstrap your startup honeypot in 15 minutes
No less then 33 minutes after the sneakpeak screenshot, we were able to stand up a "course registration" site which included a domain name and registration form that would log the perspective students email. In fact, we didn't even require the full 33 minutes to do this - we only started working on it around 15 minutes after the sneakpeak.
Step 1: Register a domain
We knew from past experience that registering a domain on AWS Route53 would probably take ~10-15 minutes, so we decided to do this so we could let the process complete in the background. Registering a domain on AWS Route53 is as simple as checking avaliability and paying 10-12$ USD to register it.
Step 2: Make the registration page
We suck at web development, so we asked Anthropic's Claude LLM to generate a registration form for us. This was the first version that it made for us. We added some additional code to log the email address back to our server.
document.getElementById('emailForm').addEventListener('submit', function(e) {
e.preventDefault();
var email = document.getElementById('email').value;
var xmlHttp = new XMLHttpRequest();
xmlHttp.onreadystatechange = function() {
if (xmlHttp.readyState === XMLHttpRequest.DONE) {
alert("Successfully registered! Check your email for the invite link. If you did not receive an email, tweet @thoughtfault for support.");
}
};
xmlHttp.open("GET", "https://register.black-team-ops.com/register?email=" + email, true);
xmlHttp.send();
});
We also had it generate HTML for us, we think it turned out quite pretty

Step 3: Deploy the EC2 instance
Next, we launched an AWS EC2 instance and installed apache and certbot. Our domain had finished registering at this point, so we modified the hosting zone to include a "register" subdomain, requested our SSL certificates from LetEncrypt, and had a functioning SSL enabled registration logger.
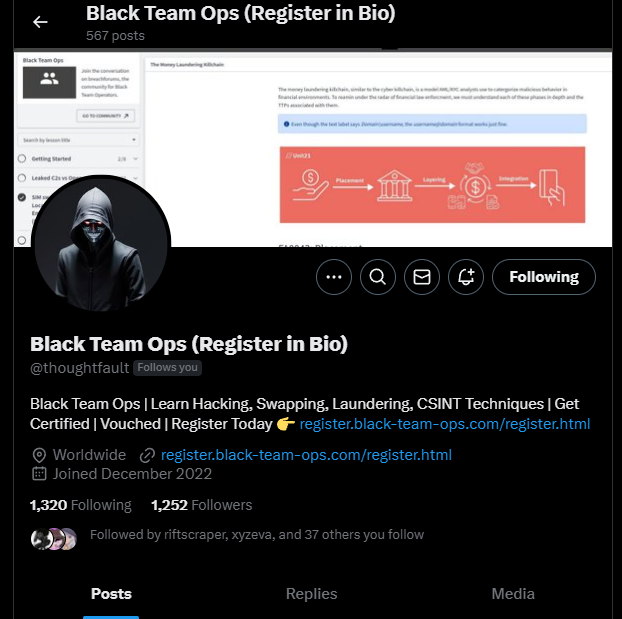
Step 4: Shill our course
Armed with our pretty looking registration page and knowledge from introductory level college marketing classes, we began unapologetically spamming the link to our website. We also changed our bio and profile picture for extra realism.
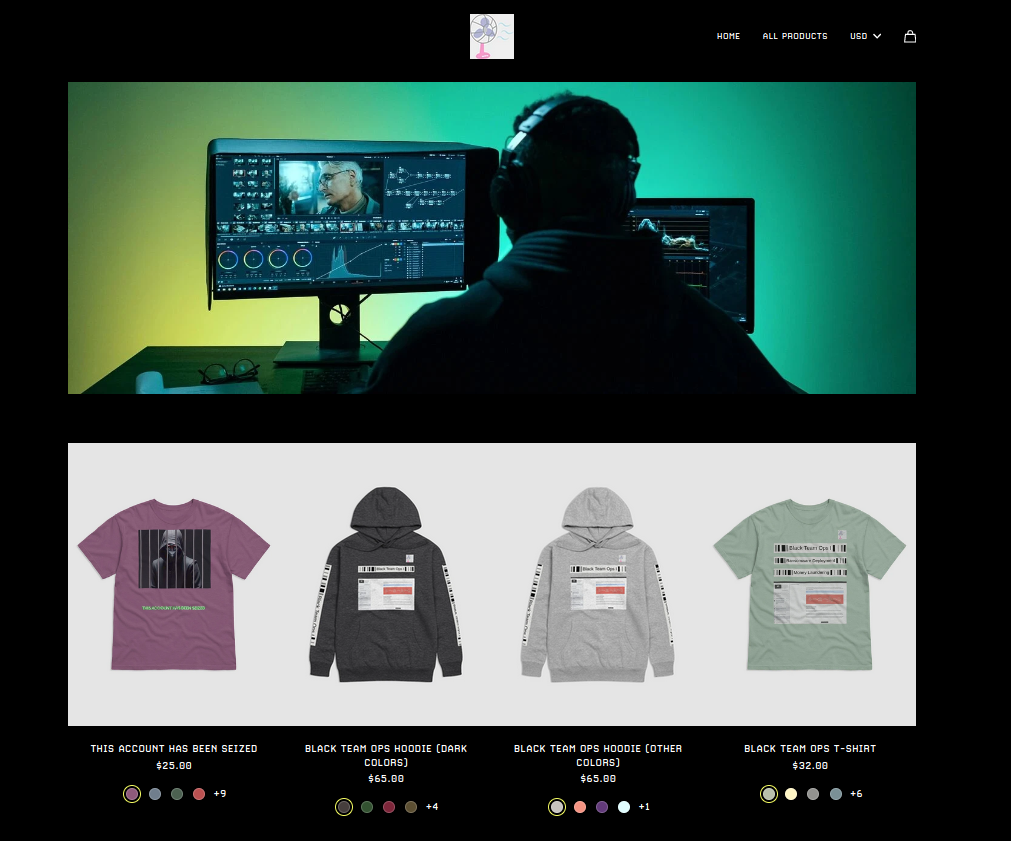
Step 5: Shill our merch
We also started a Black Team Ops themed merch brand. Sadly, only 2 purchases have been made so far.
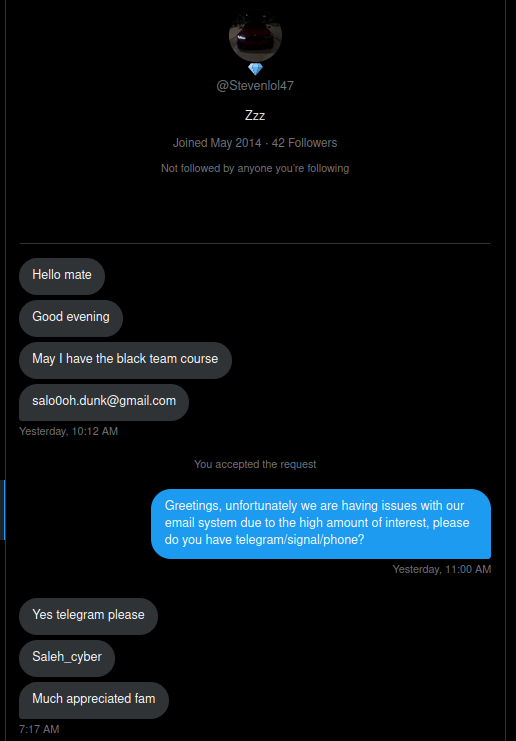
Step 6: Collection
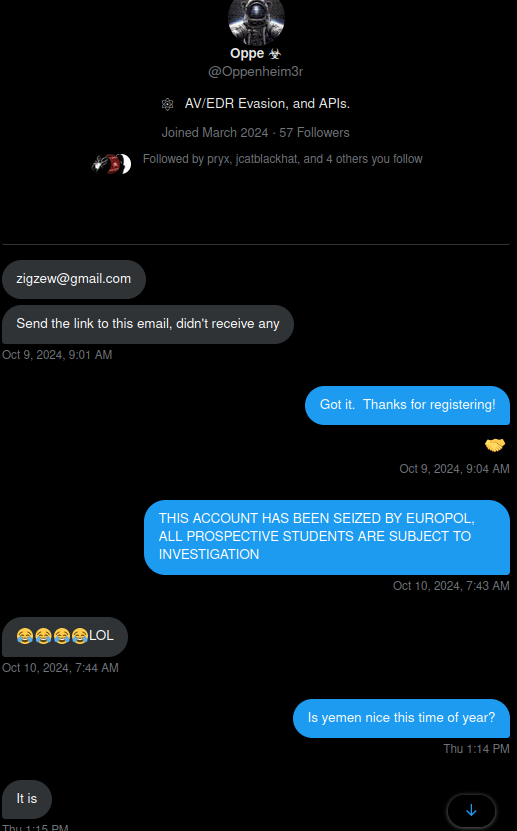
We received a lot of messages asking for support since they were not getting the email for the course. Of course your not, its a honeypot 😁. We used these as a chance to gain an additional point of information about prospective students, such as telegram handles.
Step 7: Scare the shit out of every prospective "Black Teamer"
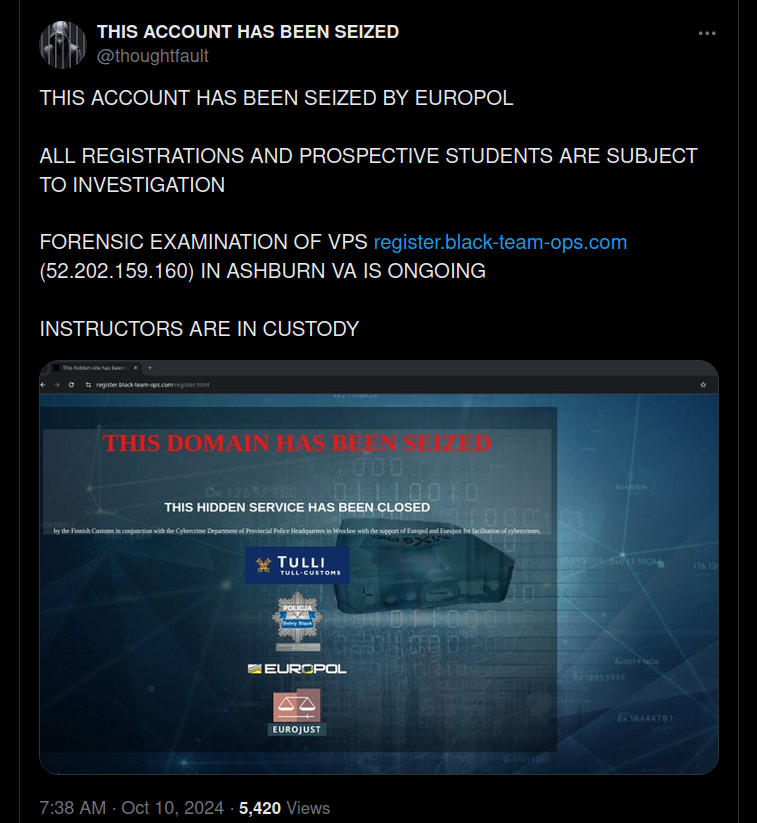
Although "Black Team Ops" was never a real course, the one thing we hope prospective students to learn is to use burner emails/accounts/vpn/tor for most sites, especially ones like these!
We decided to scare the shit out of people who registered by pretending law enforcement had seized the domain (and that they were subject to investigation). We followed up to everyone who messages us telling them this. (deepest apologies to @inarirecon a CTI person who we also messaged)
We also found a joke seizure page on GitHub and put it up on the site
INTERMISSION: The Curious World of Script Kiddies: A National Geographic Special By David Attenborough
As we venture deeper into the digital undergrowth, we come across a particularly fascinating specimen known to the local fauna as @Oppenheim3r, whose online behavior provides us with a textbook example of the skid in its natural habitat.
IP: 175.110.26.40 (Taiz, Yemen)
EMAIL: zigzew@gmail.com
TWITTER: @Oppenheim3r
The skid in it's natrual habitat, hoping to one day be a millionare and FBI's most wanted but lacking the competence to do so. Prefers to be a cybercriminal type shit
This also serves as a mating call, attracting other skids to breed with it and hunt their prey together: unsuspecting grandmothers
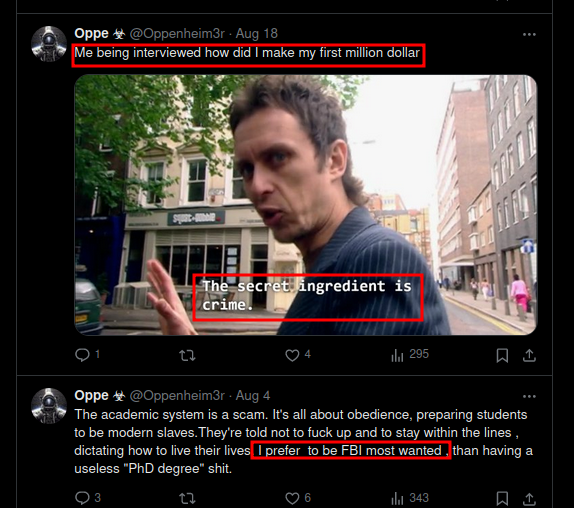
In a fascinating display of cognitive dissonance, we witness the skid seething with frustration over its inability to secure employment as a cybersecurity professional. In a remarkable twist of logic, it proclaims that this rejection will inevitably drive more skilled individuals – among whom it counts itself – into the murky waters of cybercrime.
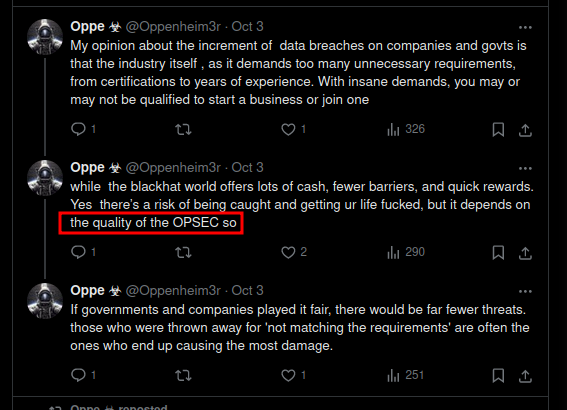
The skid, in its infinite wisdom, posits a theory: if one's operational security, or "OPSEC" as it's known in these circles, is sufficiently robust, the potential rewards of cybercrime outweigh the risks. It's at this point, dear viewers, that we observe a spectacular example of the Dunning-Kruger effect in action.
Our subject's own OPSEC, you see, is about as watertight as a colander. In a display of digital ineptitude that would make even the most novice IT professional wince, we watch as the skid unwittingly leaves a trail of breadcrumbs across the internet. Its residential IP address, email, and Twitter handle are strewn about the digital landscape with all the subtlety of a elephant in a china shop.
Step 8: Make pew-pew map
We pulled the apache logs from our ec2 instance and grepped for "/register" and "/regsiter" (we cannot spell). We then used the following library to parse the logs (https://github.com/amandasaurus/apache-log-parser).
We extracted a unique list of IP addresses that registered from the parsed logs and fed them into this pew-pew map (https://github.com/ammaraskar/GeoIP-Scraper/tree/master)
To build our pie chart, we used some bash magic
for ip in $(cat ips.txt ); do curl ipinfo.io/$ip | jq -r ".country" | tee -a geolocation.txt; done
cat geolocation.txt | sort | uniq -c | sort -nrk 1 | sed 's/^\s*//g' | tr ' ' '\t' > geolocation.csv
We imported all the data into google sheets to map the geographic distribution of the registrations.
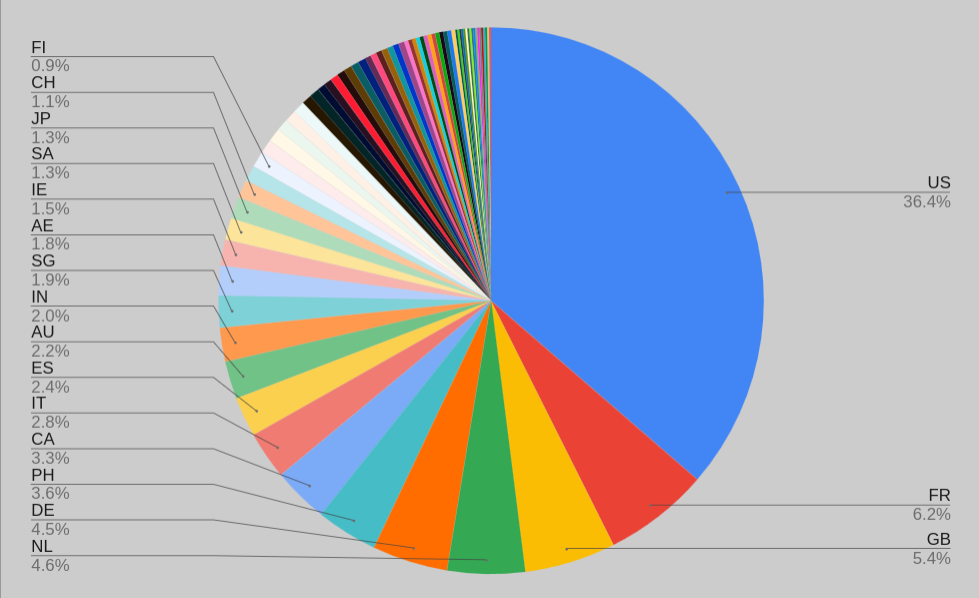
The data in tab-delemited format: we were surprised that despite China and Russia being most heavily associated with cyber shenanigans, interest was higher in other non-English speaking countries such as France
309 US
53 FR
46 GB
39 NL
38 DE
31 PH
28 CA
24 IT
20 ES
19 AU
17 IN
16 SG
15 AE
13 IE
11 SA
11 JP
9 CH
8 PL
8 FI
7 QA
7 MY
6 IL
6 DK
6 BR
5 RO
5 ID
4 TR
4 PT
4 CZ
4 CL
4 BE
4 AT
4 AR
3 UA
3 SE
3 MX
3 KW
3 GR
3 EG
3 EE
2 ZA
2 YE
2 TW
2 RS
2 NZ
2 NO
2 MA
2 LK
2 KR
2 KE
2 EC
2 CO
2 AL
1 UY
1 TT
1 TH
1 SK
1 SI
1 RU
1 OM
1 NG
1 LU
1 HU
1 HR
1 HK
1 GH
1 GE
1 CN
1 BG
1 BB
1 AM
Step 9: Funny stuff
Someone scripted something to rickroll us through the registration page
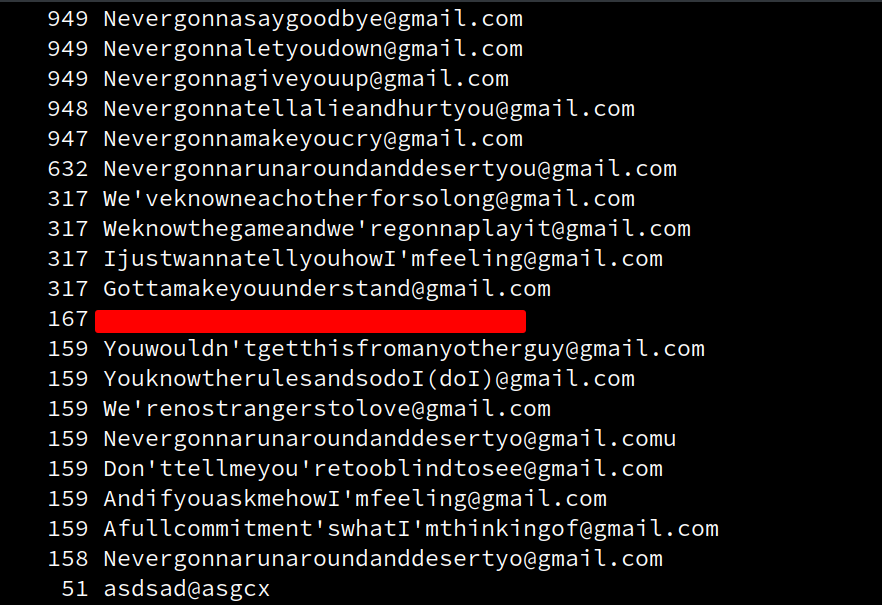
Someone started gobusting us after they attempted to register.
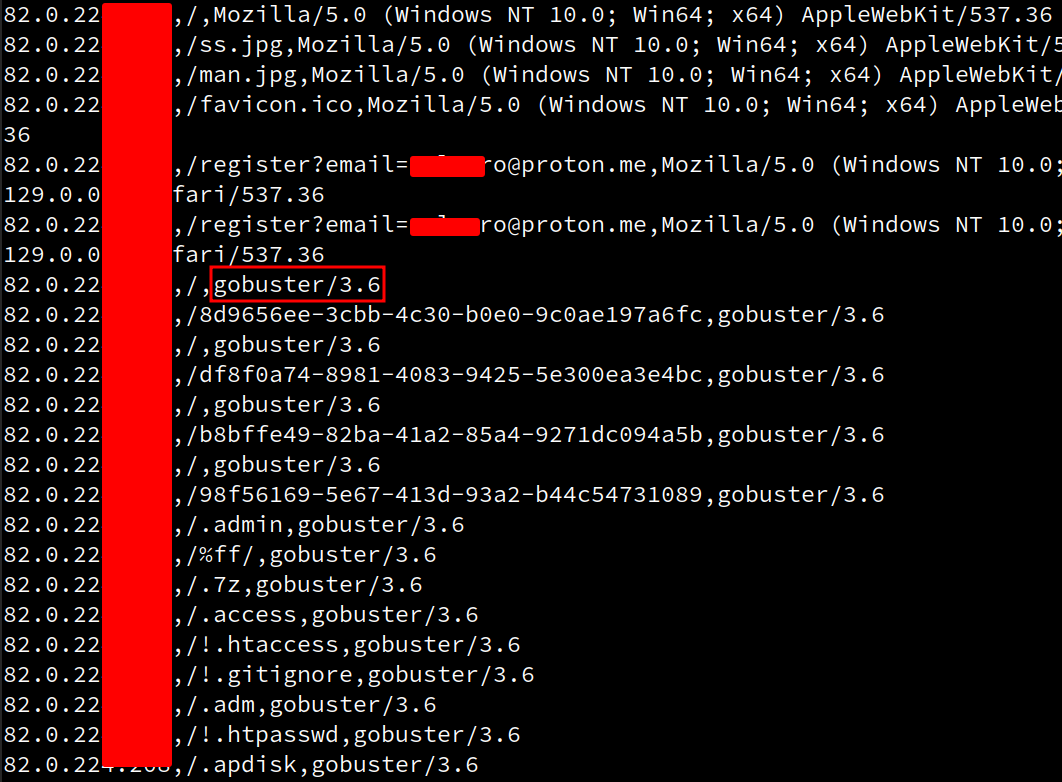
And of course, a variety of expletives and slurs were sent as emails.
Conclusion
While Black Team Ops was never a real course, we were surprised by the number of registrations, especially those coming from non-english speaking countries. SIM Swapping and people wanting to learn it is definitely on the rise. One of the TA groups, SCATTERED SPIDER (attrib by CrowdStrike) also engages in smishing, social engineering and sim swapping tactics.
SpatialSec Protections
As a corporate threat intelligence team, we would have no incentive to provide intelligence to the public without using it as an oppurtunity to shill our product which conveniently addresses the threats in the report. With that being said, we present:
SpacialSec CTIStream™, a novel cyber HUMINT driven IOC collection system. Customers with CTIStream™ have access to the IP addresses collected within this blog post (which belong to current and prospective threat actors), easily accessible from a REST API that defenders can incorporate into their threat hunts.
If you are interested in demoing CTIStream™, please send a DM to @thoughtfault (https://x.com/thoughtfault) to schedule a call with one of our sales engineers.
Please remember we also sell office fans
It's literally an office fan on a default setting
You have an AC outlet, right?
Whether adversary nation or criminal actors, SpatialSec™ will be sure to blow papers everywhere
Our properitary office fans™ will be updated over the air for god knows what reason